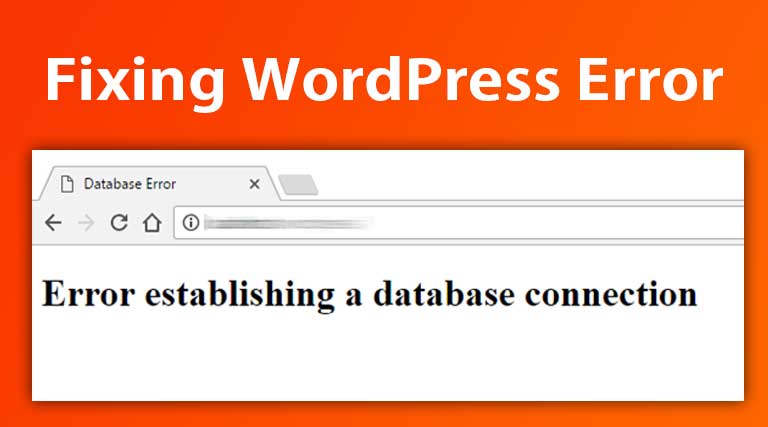
 One day you discover with horror that in the search results there are references on your website to pharmaceutical products. You check the content and find strange links to websites that should not be there … To make matters worse, your site is listed as dangerous by Google, with the bad image that implies facing the outside. And now what do I do ?, you ask. Don’t worry! In this article, I will show you how to remove malware from your WordPress hacked site easily.
One day you discover with horror that in the search results there are references on your website to pharmaceutical products. You check the content and find strange links to websites that should not be there … To make matters worse, your site is listed as dangerous by Google, with the bad image that implies facing the outside. And now what do I do ?, you ask. Don’t worry! In this article, I will show you how to remove malware from your WordPress hacked site easily.
Keep Calm, FundamentalHow to Remove Malware From WordPress Hacked Site
The first reaction will be to experience great stress, overwhelm and hurry to solve the problem. In such a situation it is easy to make mistakes and even carry out hasty actions that may turn out to be irreversible.
So, the main thing is to keep calm, take a deep breath and carefully follow the instructions:
1. Active “MAINTENANCE MODE”
In this way you will avoid giving bad images and that both users and search engines detect unwanted activity. You can do this in two ways: installing the WP Maintenance Mode plugin or, if you have experience editing code, you can do it manually in the following way:
1.1. Create a file in the root that you can call for example “maintenance.php“.
1.2. Edit this file that you just created and design it to your liking. To simplify things, a simple code example would be the following:
<html>
<h1>Estamos realizando tareas de mantenimiento.</h1>
<h2>Por favor, vuelva a intentarlo más tarde. Disculpe las molestias.</h2>
</html>
1.3. Edit the functions.php file of your WordPress theme and add the following code:
function modo_mantenimiento() {
global $pagenow;
if ( $pagenow !== ‘wp-login.php’ && ! current_user_can( ‘manage_options’ ) && ! is_admin() ) {
header( $_SERVER[“SERVER_PROTOCOL”] . ‘ 503 Service Temporarily Unavailable’, true, 503 );
header( ‘Content-Type: text/html; charset=utf-8’ );
if ( file_exists(ABSPATH . ‘mantenimiento.php’) ) {
require_once(ABSPATH . ‘mantenimiento.php’);
}
die();
}
}
add_action( ‘wp_loaded’, ‘modo_mantenimiento’ );
With this we manage to prevent our users from seeing strange things on our website and, on the other hand, we keep intact the ability to access the WordPress administration.
2. Identify the Problem to Remove Malware
The next step is to try to identify the problem. For this, you can visit the Google diagnostic website and see if your site is infected with malware. Also, I recommend you use the free Sucuri tool to identify the problem and remove malware your WordPress site.
Surely now you already have some more information. With this, plus the symptoms that you are experiencing on your website, I recommend that you contact your hosting company to communicate the problem and follow their instructions. This is very important, especially in shared accommodation, since the attack may have affected more than one site. If the technical service leaves much to be desired and is not for the task of offering you help, consider changing your hosting company at the end of this guide.
3. Analyze Your Team
Believe it or not, it is very common that the equipment we use regularly is the main source of all problems. Make sure you have a good antivirus installed and updated, and perform a full scan. There are very good solutions in the market such as Kaspersky Antivirus, Panda Global Protection, etc. It is also good to complement it with tools specialized in detecting malware, such as Malwarebytes Anti-Malware.
4. Make Backup of the Site and Database.
Fundamental, before making any changes, make a Backup of the website and the database. In this way, you will avoid risks of loss of information if something goes wrong. This copy leaves it saved separately.
5. Change All Passwords to Remove Malware WordPress
It is imperative that you change all passwords to prevent attackers from continuing to act on your website:
- WordPress Access: change the password of all users. Verify that no administrator users have been added that should not be. Remove any user that you consider suspicious.
- Control panel of the accommodation.
- FTP
- Database.
When modifying the password of the database, you must immediately edit the wp-config.php file and write the new password, otherwise, WordPress will not be able to establish a connection with the database and your site will be inaccessible.
Also, in this same file, you must change the security keys. To do this, access the official WordPress security key generator, copy the generated code, and replace it where appropriate in the wp-config.php file.
Take advantage that you are editing it to make sure that there is nothing strange about it.
6. Remove Malware From WordPress.
We are ready to start to remove Malware From WordPress:
6.1. If you use a cache plugin, I recommend that you disable it and clean the cache, because if an infected file is left in the cache, it can leave your site infected again.
6.2. Install the WordFence plugin or Anti-Malware Security and Brute-Force Firewall in order to perform a check of your website. So you can see which files seem infected, which lines of code have been inserted and where. This is essential if you use a custom theme of your own.
6.3. Download your theme, which is inside the folder / wp-content / and check and edit the files according to the instructions of the security plugin. As a result, you will have your clean theme on your computer. To make sure, you can analyze the files of your theme with your antivirus and your antimalware tool. If you use a commercial theme, I recommend that you download a clean copy from its official site.
6.4. Enter the plugins section of your WordPress installation and note the plugins you have active and download the most updated versions of them on your computer.
Very well. For now, we have a clean theme and plugins.
Check the content of your website and look for iframes, rare codes, internal and external links that point to suspicious sites to eliminate them.
6.5. Now connect via FTP and sort the files by modification date. Pay special attention to the last modified ones, since usually, they are usually those that contain malicious code. Download the latest version of WordPress from the official site. Unzip the downloaded file in a folder on your computer. Check that folder and file structure and compare it with the one on your server. This way you can detect strange files that should not be.
6.6. Sometimes you may find that it is not possible to remove all the malicious code. In that case, the most advisable thing is that you replace the files of your WordPress installation with the WordPress files downloaded from the official site.
- Remove everything in the root except the / wp-content / folder, the .htaccess file and the robots.txt file, which you’ll have to check for nothing unusual.
- In the folder / wp-content / you will see the following:
1) plugins: you should remove all the plugins and insert the new versions that you downloaded on your computer before.
2) themes: delete all the themes and upload your clean theme only on your computer.
3) uploads: check that there are no .php executable files. If there were, eliminate them.
4) index.php: check that it does not contain malicious codes - At this point, upload the copy of WordPress that you downloaded. Regardless of the / wp-content / folder and the wp-config.php and .htaccess files, which you already have ready on your server.
Check that everything works correctly and, finally, delete or leave a comment on the function you created at the beginning of the article and thus disable the “maintenance mode”.
6.7. Finally, access the webmaster tools of Google and ask them to review your website. If you do not know how to do it, you can check Google’s help.
7. Prevents Future Attacks
You already have your site clean and perfectly operational. However, to avoid as much as possible that you see yourself again in compromised situations, it is essential that you adopt the following measures:
7.1. Change the prefix of your database. You can use the Change DB Prefix plugin. Of course, as always, before any major change, make a backup of your database.
7.2. Modify the permissions of the files hosted on your server to 755 and directories to 644. Forget about granting 777 permissions to files or directories. Do not give facilities.
7.3. Generates empty index.php files to prevent directories from being accessible through the browser.
7.4. Check that the user “admin” does not exist, since it is the first one that the possible attackers look for.
7.5. Create a .htaccess file with the following code:
<Files * .php>
deny from all
</ Files>
And place it in the / wp-content / uploads folder. This way you will avoid running .php files inside the “uploads” folder, something that many attackers usually try.
7.6. Performs periodic backup copies of both the website and the database. And save it somewhere safe, if possible outside the hosting server.
7.7. Keep your WordPress updated, as well as the theme and the plugins that you use.
7.8. Remove comments of type spam. You can help plugins like Akismet or Antispam Bee.
7.9. Activate a security plugin such as Wordfence, All In One WP Security & Firewall or iThemes Security.
7.10. Always use strong passwords and educate your collaborators in the vital importance of this practice. To make your life easier, you can use this online password generator.
Have you ever attacked your website? Have we left a step that you consider important? Do you know any plugin or efficient tool in the detection/prevention of attacks? Share your experience with us and, if you need help, do not hesitate to contact us.

 My Account
My Account 


 USD $
USD $  BDT ৳
BDT ৳